If you’re in the process of building a new mobile app, enterprise software platform, or require help establishing a cloud data environment, it’s important to consider your security measures. It’s easy to get complacent about data security — until something bad happens and you’re left scrambling to sort out damage control. For this reason, it’s prudent to have a basic understanding of the types of encryption, which is one of the most important elements of your data security strategy.
What is Encryption?
Encryption is, at its core, a secret code. A piece of data is encrypted and later, unencrypted using a key, which you can think of as the secret code’s cipher.
When data is encrypted, it is protected since it’s unreadable to anyone who may access the data — unless they have the ability to decrypt the data. But modern encryption is so sophisticated that it’s virtually impossible for a layman to decrypt; you would need sophisticated software and tremendous computing power.
What Are the Different Types of Encryption?
There are many different types of encryption, with the most basic two forms being symmetric encryption and asymmetric encryption. To understand these forms of encryption, you must have a good understanding of the process used to encrypt and decrypt a piece of data.
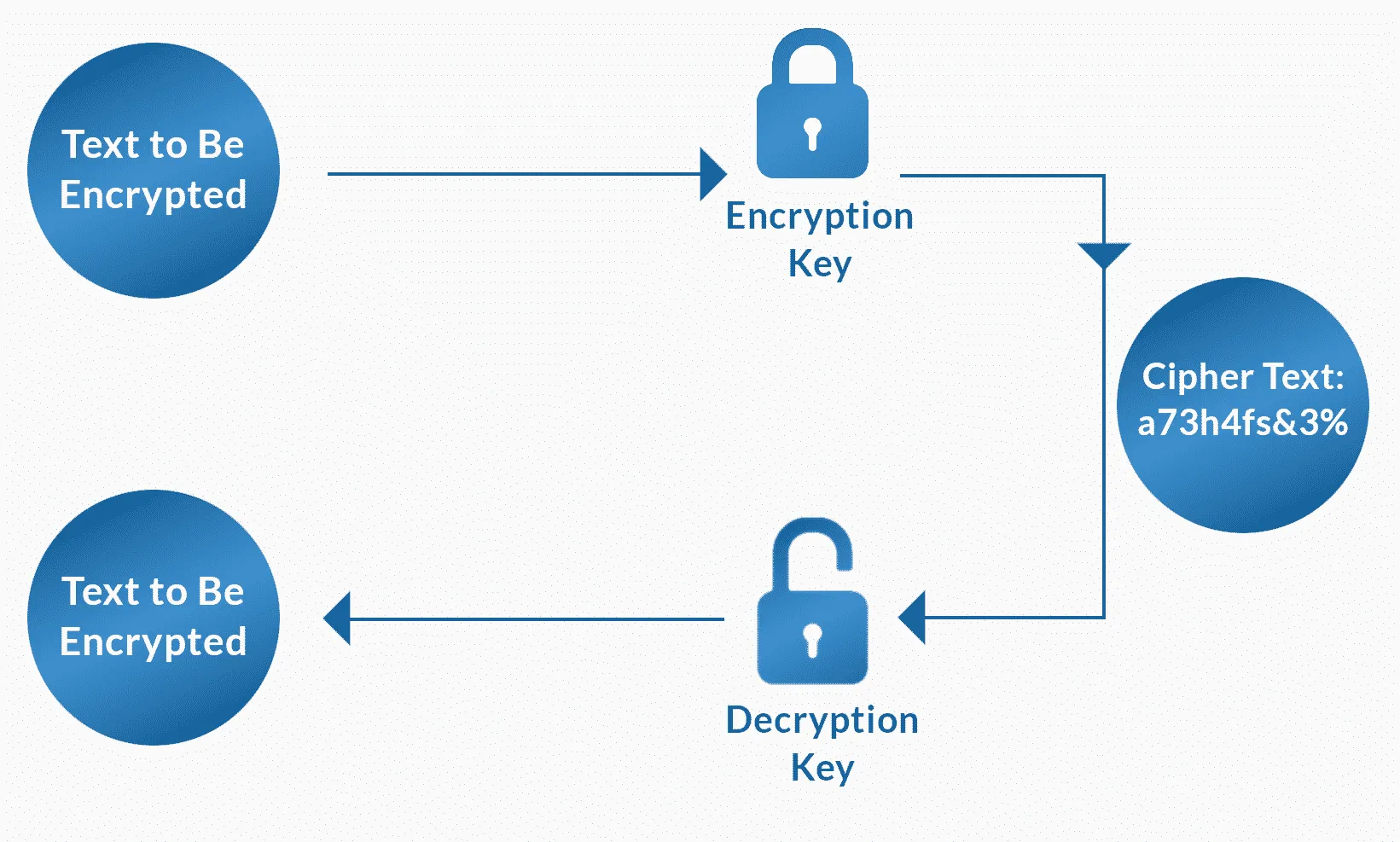
As the graphic below illustrates, you begin with a piece of data to be encrypted, in this case, a piece of text that says “Text to be encrypted.” This data is processed by the encryption key, which results in cipher text — encrypted text that’s in a sort of “secret code” language.
The data remains encrypted until a user decides to decrypt the information. So the data is processed through a decryption key and the cipher text is transformed into its original form — “Text to be encrypted.”
In the case of asymmetric encryption, you typically have a public key used to perform the encryption and a secure private key is used to decrypt the data. This type of encryption is preferred method in many cases involving data transmission from point A to point B; otherwise, you’re tasked with finding a highly secure method for passing the encryption key to the recipient. If that key is intercepted, the interceptor could theoretically encrypt and decrypt your data.
What is Bit Encryption?
It’s common to hear about 256-bit encryption, which is one of the more secure encryption options. 128-bit represents a moderate degree of encryption, while 40-bit is less secure.
The term “bit” refers to a single piece of data — a single bit represents a single character (such as a letter or number.) So in the case of 256-bit encryption, the key is 256 characters long. In the case of 40-bit encryption, there are 240 possible keys — that’s about one trillion.
In the case of 128-bit encryption — which, in conjunction with 256-bit encryption, requires a special algorithm — is regarded as “logically, unbreakable” due to the tremendous computation power and time that would be required to arrive at the proper combination of characters. There are 2128 different combinations for the 128-bit encryption key.
A cracker attempting to crack a 256-bit encryption key would need to try 2256 different combinations to successfully decrypt data. This type of encryption is most commonly used for SSL certificates and other scenarios where potentially-sensitive data is being transmitted across a network or over an internet connection. Financial institutions, government agencies and the military also uses 256-bit encryption for all of its data. In fact, the U.S. government requires all potentially-sensitive data to be encrypted using 192-bit or 256-bit encryption methods.
There are even stronger forms of encryption in existence, such as AES256 encryption, which is a derivative of Rijndael encryption. This type of encryption has gained popularity in recent years.
Is Hashing a Form of Encryption?
In short, hashing is commonly mistaken as one of the forms of encryption. Hashing is a technique that’s used to generate a series of numbers, letters and symbols to summarize your data.
Hashing is used in combination with cryptography. For instance, hashing can be useful for creating digital signatures and other “integrity controls.” But there is no “secret key” associated with hashing and the hash can be recreated, so it lacks the security of true encryption.
As a top Dallas custom software development company, 7T strives to solve problems and boost ROI through digital transformation. Security is always on our radar and we have lots of experience developing mobile app and custom software platforms with military-grade security. Our innovative team integrates cutting-edge solutions into virtually every development project, whether it’s mobile app development, custom software projects such as CRM platforms or ERP development, or Snowflake data solutions. We’re ready to deliver collaborative, multi-phased software development services to clients in all business sectors.
As a top Dallas custom software development company, 7T strives to solve problems and boost ROI through digital transformation. Security is always on our radar and we have lots of experience developing mobile app and custom software platforms with military-grade security. Our innovative team integrates cutting-edge solutions into virtually every development project, whether it’s mobile app development, custom software projects such as CRM platforms and ERP development, or Snowflake data solutions, we’re ready to deliver collaborative, multi-phased software development services to clients in all business sectors.
7T has offices in Dallas, Houston, Chicago, and Austin, but our clientele spans far beyond Texas and the midwest. If you’re ready to harness the power of a highly secure mobile app, custom enterprise software platform and today’s most innovative technologies, contact 7T. We invite you to call our Dallas area offices at 214-299-5100.










